Running Networks in the World of Android: Shadow of the Beanstalk
Shadow of the Beanstalk is a near future campaign setting book released by Fantasy Flight Games in 2019. This book is intended to be used with Fantasy Flight Games’ Genesys role-playing rules. Shadow of the Beanstalk uses the Android setting as its background setting. Android was a board game originally published in 2008, having several such games released over the years. Perhaps more well known is that Android was used as the basis for a popular collectible card game, Android: Netrunner.
Android, and by extension, Shadow of the Beanstalk is a cyberpunk, science fiction universe, set primarily on Earth in a mega city called New Angeles, though extensive populations live on the Moon and Mars. Dark and gritty, Android features many of the tropes of cyberpunk literature and film: flying cars, extremes of poverty and wealth, barrages of consumer-focused media. As with any cyberpunk setting worth its salt, hacking, or running in Android lingo, is a common activity. While the Genesys core rules cover hacking, given the more complex and embedded nature of running in Android, supplementing the rules for the setting made sense. The result is one of this writer’s favorite ways of conducting computer hacking encounters in a tabletop role-playing game.
The principle is straightforward: the runner wants to get into a network for some reason — steal information, wreak havoc, whatever. The owner of the network wants to keep keep the runner out — the opposition to the runner is the sysop, short for systems operator. One of the challenges around running in RPGs has been that the encounter is either disassociated from the remainder of the party or it becomes a solo encounter occupying a lot of time as the other players lose interest, look at Facebook, or buy things off the Internet. Shadow of the Beanstalk aims to solve this by allowing the encounter to be embedded seamlessly with other social (rest of the party is at a night club attempting distract a group of corporate execs while the runner steals their money) or combat encounters (the party is attempting to infiltrate a building and the runner is turning off cameras and defenses).
Thus, in addition to actions and maneuvers like aiming, shooting, moving, and so on, the runner and sysop have actions like Access System, Burn System, Break Ice, Trace User, Lockout, and Sweep and maneuvers like Enact Command and Activate Program. Actions require a dice roll, while maneuvers usually do not. During a runner’s or sysop’s turn they can perform these just like regular players do their actions and maneuvers. Additionally, the runner can be shallow or go deep — either be aware of the existing surroundings and typing away on their computer or entering cyberspace fully and using brain-machine-interfaces (BMIs) to conduct their work in the virtual world. While integrating the runner’s turns in with the other players sacrifices the idea that in cyberspace one can do much more because they are using their mind to control actions, it allows for seamless blending into the game — ensuring all have fun at the table.
The game master (GM) sets up what a network looks like — what the systems are (camera control, files revealing corporate corruption, security door controls, air-conditioning system, whatever) and the security programs that protect those systems. These are pulled from the Netrunner game and are called “ice”— intrusion countermeasures electronics. Theses are software programs like Fire Wall, Sentinel, and Enigma.
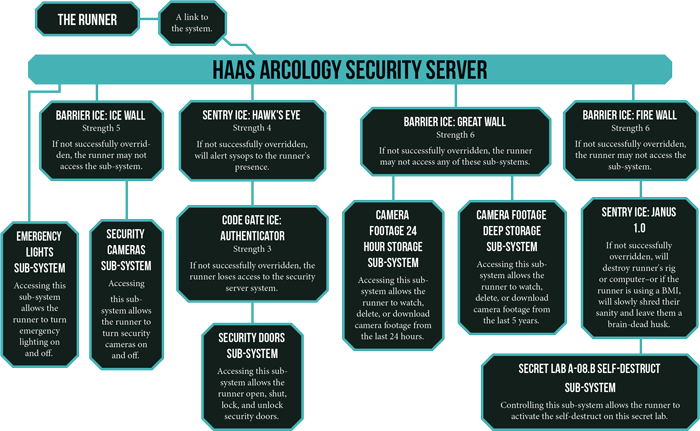
The book provides an example network.
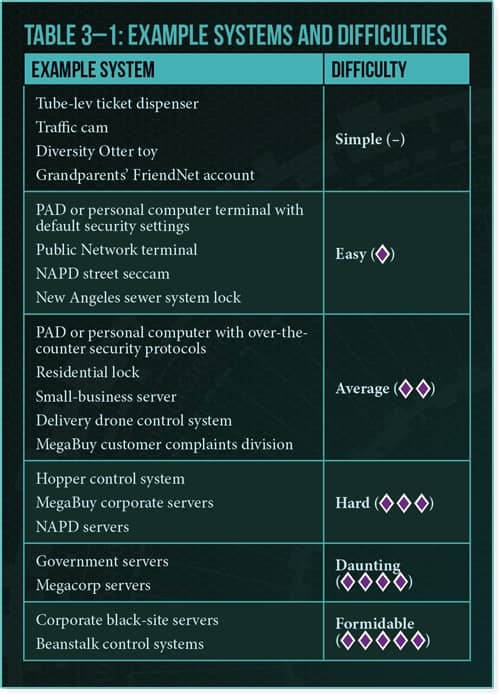
When the runner first encounters this, she knows nothing about the ice or sub-systems. To do that, she first needs to break into the security server. The difficulty of the roll is dependent on the level of the system. This can range from Simple (no roll needed) for things like a traffic camera to Formidable (five Difficulty dice) for corporate black site servers. Genesys uses the same narrative dice system as Fantasy Flight Games’ Star Wars RPG — with different symbols. This means the dice rolls tend to produce not just failure or success but also good and bad additional results — Advantage and Threat, respectively. Thus, as our runner maneuvers through the system, those begin to come into play. For example, if the runner is up against this corporate Haas Arcology server, the task is Daunting (four Difficulty dice). She rolls and ends up with a success but also an Advantage. This may mean that as she’s breaking in, she notices a secondary network node that will allow her access in the future, which might come in handy if she is discovered and gets locked out.
Once the runner, let’s call her Alloy Deck, enters the system, she can see all the sub-systems — unless the GM wants to hold back a special one. She would also see that ice is protecting other sub-systems but not what that ice is. During her turn (perhaps the rest of the party is attempting to break into the arcology), the runner can move to one of the nodes. Alloy Deck can get to the Emergency Lights sub-system with no issue because no ice is protecting it, but she wants to go the Security sub-system. Once she says she wants to go there, she hits the ice and sees what it is. On first encountering it, Alloy Deck must try to break it. Breaking protective software can be attempted purely with a skill roll and no additional help. If, however, the player has loaded up a piece of ice breaker software into their computer (most computers have limitations on the number of active ice and ice breaker software that can be running at one time), she can attempt that.
All ice have a program strength. The Ice Wall protecting the cameras sub-system has a program strength of five. Ice breakers provide an override strength. So our runner hits that Ice Wall and immediately must attempt to break it. She rolls her dice pool with an Average difficulty (two Difficulty dice) and ends up with with four total success. This in and of itself will not overcome the Ice Wall’s five program strength. If the runner has an appropriate ice breaker active — one that affects barrier ice like Ice Wall — she can use that ice breaker’s override strength as additional success to her roll. For example, Alloy Deck had Corroder up and running on her computer. Good news, Corroder affects barrier ice and provides four override strength. The runner can add that four to her four for a total of eight successes, breaking through the Ice Wall. The runner on her next turn could then go into the Camera sub-system and turn them off (or put them on a loop or something).
The different ice and ice breakers provide for different effects on success and failure as well. Failures might result in damage to the software or computer…or even to the runner if Alloy Deck is using a brain-machine-interface. Advantage and Threats rolled for breaking ice and whatnot can result in making it easier or harder to trace the runner, scouting ahead and learning what ice could be encountered, or locking down systems. The narrative dice system’s Triumphs and Despairs are escalations of these options.
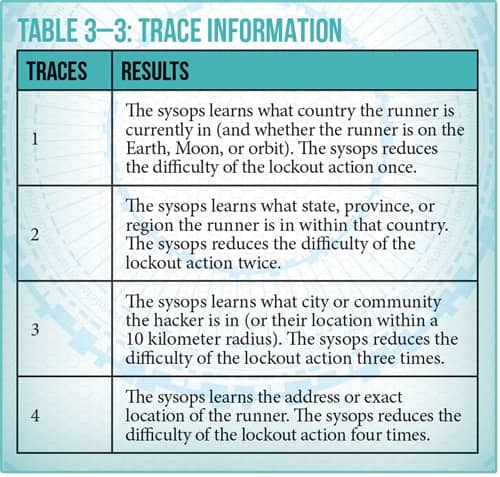
Of course, the GM is controlling the sysops protecting the system. Once they learn of an intruder (perhaps a Threat on one of Alloy Deck’s rolls flashed a small alert to the sysop, who sees it and recognizes the danger), they can begin shutting down the system to force out the runner (takes time and successful dice rolls) and other actions, including tracing the runner to his or her real-world location and dispatching a hit team. The Sweep action functions as a patrolling guard in the system.
Running and countering runs gels well with the Strain mechanic that Genesys uses. Strain is a derived statistic used to represent stress and other effects. Characters spend Strain for an extra maneuver in encounters. Running dice rolls often result in incurring deficits to Strain. For running, this is a natural fit. As the encounter progresses, Alloy Deck and the sysop accumulate hits to their Strain as Advantage and Threat appear on the rolls–cinematically, this is the sysop sweating as he tries to find Alloy Deck and stop her from getting to the self destruct; for Alloy Deck, this is her grimacing in cyber-pain as she dodges the sysop’s roving cyber-guards.
On the Fantasy Flight Games forums, a Drainsmith, a frequent contributor to them, released a set of cards for network encounters. These are great supplements to any game with a network encounter. As the runner begins, the GM can lay out the cards, showing the network structure, and flip them as the runner encounters ice or secret sub-systems. Using the Haas arcology example, the initial view of the network would look like this:
Then after hitting the Ice Wall, the GM would flip the card and reveal. As per the rules, the runner knows where ice is but not what specific ice she will find.
The rules for network encounters as presented in Shadow of the Beanstalk are, to date, the most enjoyable rules for fun, fast-paced running and hacking in tabletop RPGs I have seen or played. Sacrificing some realism in the service of fun and leveraging the mechanics of the narrative dice system, they have proven to be dynamic and blend seamlessly with other action.
Patrick Kanouse encountered Traveller and Star Frontiers in the early 1980s, which he then subjected his brother to many games of. Outside of RPGs, he is a fiction writer and new convert to war gaming. His last post for Black Gate was Telling Your Star Wars Story with Dice Rolls. You can check out his ongoing, play-by-post, referee-less Traveller game at basiliskstation.blogspot.com. Twitter: @patrickkanouse. Facebook: www.facebook.com/patrickkanouse





The netrunning system in Shadow of the Beanstalk seems to be a streamlined version of the old Shadowrun rules for “deckers”, including the ideas to integrate net hacks into concurrent IRL jobs. Is that a fair comparison to make?
Eugene, hello! It has been so long since I played Shadowrun, which I never played a lot of. I’ll have to bow to your knowledge on this. 🙂